How the Allies miraculously cracked the secret Nazi and Japanese codes during WWII

The clattering of typewriters and the hum of early computers hidden inside a small manor in the English countryside was the site of one of WWII's most pivotal battles: codebreaking.
At Bletchley Park, brilliant minds worked tirelessly to decrypt enemy messages. It involved solving puzzles, deconstructing complex systems of cryptography, and piecing together scraps of valuable information, at any moment, trying to walk the line between life and death for millions of people.
Thanks to relentless determination, a legion of codebreakers finally found the secret to the complex Enigma and Japanese codes to slowly turn the tide of war in the Allies’ favor.
The development of secret codes between the wars
Before the outbreak of the Second World War, nations like Britain, Germany, and Japan had invested heavily in the development of secret codes to secure their communications, both in military and diplomatic contexts.
In particular, the British Government Code and Cypher School (GC&CS) was established in 1919, which was initially focusing on diplomatic codes.
They were exploring different kinds of encryption systems that employed a mix of manual and machine-based methods to encode their messages.
On the other side of the world, Japan had developed two kinds of codes, named ‘Red’ and ‘Blue’.
The Red code, which was introduced in the 1920s, used a polyalphabetic cipher, which employed multiple substitution alphabets to encrypt messages.
This made it more secure than simpler, single-alphabet ciphers. However, the ‘Red’ code eventually became vulnerable to cryptanalysis, leading to the development of the slightly more advanced ‘Blue’ code in the 1930s.
In addition, Japan developed military encryption systems, such as the JN-25 naval code in the mid-1930s.
This was a highly complex codebook system that used numerical ciphers to encrypt messages.
Each group of numbers corresponded to a specific word or phrase, based upon frequent changes to the codebooks to enhance security.
Furthermore, the use of the far more sophisticated ‘Purple’ cipher machine, introduced in the late 1930s, was a significant technological advancement, as it used an electromechanical system to encrypt diplomatic messages.
The key Allied codebreaking operations
When World War II began, the different Allied nations were instantly involved in a series of sophisticated and coordinated cryptography efforts across multiple locations.
At the forefront of these operations was Bletchley Park in Britain, where a team of brilliant cryptanalysts worked tirelessly to decipher German codes.
The facility became the center of the combined British codebreaking team. It drew on the talents of mathematicians, linguists, and engineers.
In the early years of the conflict, the team of several thousand individuals relied upon tried and tested methods to drive their codebreaking efforts.
Cryptanalysts would go on to develop a number of sophisticated statistical techniques to identify potential patterns and weaknesses in enemy codes.
For example, by analyzing the frequency of letters and pairs of letters, they could make educated guesses about the information contained in the encrypted messages.
Another significant methodological innovation was the introduction of traffic analysis.
By studying the patterns and volumes of enemy radio transmissions, analysts could infer valuable information about enemy movements and operations without necessarily decrypting the messages.
This technique provided insights into the organization and activity of enemy forces.
Based upon this, the Allies could anticipate enemy actions and respond accordingly.
The Enigma Machine
Similar to all other European countries in the inter-war years, German cryptographers had been experimenting with a range of new techniques to hide their sensitive communications from potential enemies.
One of the key innovations during this period was the Enigma machine, invented by the German engineer Arthur Scherbius in the early 1920s.
Initially intended for commercial use, the German military quickly saw its potential for secure communication.
It used a series of rotors and an electrical circuit that allowed the machine to encode messages into seemingly random sequences of letters.
Each of the rotors had 26 contact points representing the alphabet, which connected to a corresponding set on the adjacent rotor.
By changing the rotor positions daily according to a set codebook, the Germans could ensure that the encryption remained highly secure.
In addition, the Enigma machine used a plugboard, or Steckerbrett, to further scramble the letters.
This plugboard allowed operators to swap pairs of letters at any time. The combination of rotors and plugboard settings allowed Enigma to generate an astronomical number of possible configurations, making decryption extremely difficult without knowing the exact settings.
To intercept and decrypt these messages, Allied codebreakers had to recreate the exact settings of the rotors and plugboard used at the time of encryption.
How the Allies finally decoded Enigma
In 1932, Polish mathematicians Marian Rejewski, Henryk Zygalski, and Jerzy Różycki made significant strides in understanding the Enigma machine by reconstructing its wiring.
They developed techniques to deduce the wiring of the rotors, and the daily settings used by the Germans.
After the German invasion of Poland in 1939, these crucial discoveries were shared with British and French intelligence.
When Allied forces captured key German codebooks and obtained cribs (known plaintexts), it gave a much-needed boost to their decryption capabilities.
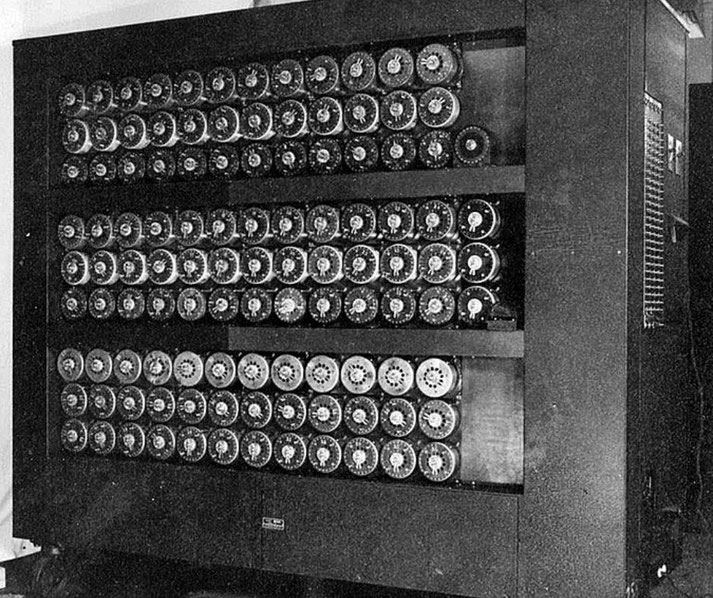
It was Alan Turing and his British colleagues at Bletchley Park that finally managed to automate parts of the decryption process by using the Bombe, an electro-mechanical device designed by Turing, which improving the speed and accuracy of their codebreaking.
In addition to the Bombe, the Colossus computer, built to decode the Lorenz cipher used by the German High Command, was the world's first programmable digital computer.
It used vacuum tubes to perform calculations at unprecedented speeds, allowing codebreakers to analyze and decrypt complex messages that would have taken much longer by hand.
Eventually, they were able to decipher thousands of German messages, which provided the Allies with crucial information about their opponent’s military plans and movements. This intelligence was known as Ultra.
Cracking the Japanese military codes
In the United States, Arlington Hall in Virginia and the Naval Communications Annex in Washington, D.C., played a similar role as Bletchley Park.
The U.S. Army's Signals Intelligence Service (SIS) and the Navy's cryptographic efforts were more focused on breaking the Japanese codes.
By 1940, American cryptanalysts had successfully decrypted the Purple code. This was thanks to William Friedman, whose team constructed a machine that mimicked the Japanese encryption device.
It ended up providing a wealth of intelligence on Japanese diplomatic communications.
The later breaking of the Japanese naval code JN-25 as well was instrumental in the American victory at the Battle of Midway in 1942.
Meanwhile, at the Central Bureau in Brisbane, Australia, there was a coordinated Allied codebreaking group for the broader Pacific Theater.
The bureau was a joint operation between American and Australian forces, focused on intercepting and decoding Japanese military communications to significantly inform the Allies' ability to counter Japanese movements, particularly in island-hopping campaigns of 1943-4.
How the decoded messages changed the war
One of the most notable examples of how decoded messages changed the war is the Battle of Midway, which took place in June 1942.
American codebreakers had successfully deciphered the Japanese naval code JN-25 by then, which told them about the details of Japanese plans to attack Midway Island.
Based upon this intelligence, Admiral Chester Nimitz devised a strategy to ambush the Japanese fleet, which resulted in a decisive victory for the United States.
The American success at this battle was so complete that it turned the tide in the Pacific Theater and weakened Japan's naval strength significantly.
In Europe, codebreaking played an equally vital role in the success of the Allies.
Before the D-Day invasion on June 6, 1944, the intelligence gathered from decrypted German communications detailed the exact location and strength of German forces in Normandy.
This information allowed planners of the invasion to try and minimize casualties and maximize the effectiveness of any assault.
Perhaps the most significant example of the impact of cryptography was in the Battle of the Atlantic.
Decoded messages from German naval communications helped the Allied fleets to counter the German U-boat threat.
They were able to track and avoid U-boat wolf packs, ensuring the safe passage of vital supply convoys across the Atlantic.
The Allies also implemented more effective anti-submarine tactics, such as the use of long-range aircraft and improved sonar.
Cryptography after WWII
Surprisingly, Alan Turing's work at Bletchley Park created the framework for much of modern computing.
His development of the Bombe and conceptualization of the Turing machine influenced the field of computer science in the next few decades.
In a similar way, the statistical techniques and pattern recognition methods used by cryptanalysts has become an integral part of modern data analysis and cybersecurity.
As a result, many businesses and governments rely upon it to protect sensitive information.
Furthermore, the success of wartime codebreaking operations highlighted the importance of intelligence in national security.
The establishment of the National Security Agency (NSA) in the United States in 1952 was a direct consequence of these efforts.
The NSA's mission included signals intelligence and cryptography, building on the work done by wartime cryptanalysts.
This agency played a critical role in the Cold War.
In Britain, the legacy of Bletchley Park continued through the Government Communications Headquarters (GCHQ), which was formed in 1946.
GCHQ inherited the cryptographic expertise developed during the war. Only after the declassification of wartime codebreaking records in the 1970s did the general public finally realize the importance of the Ultra project.
As a result, figures such as Alan Turing received posthumous recognition for their contributions.
What do you need help with?
Download ready-to-use digital learning resources
Copyright © History Skills 2014-2025.
Contact via email
With the exception of links to external sites, some historical sources and extracts from specific publications, all content on this website is copyrighted by History Skills. This content may not be copied, republished or redistributed without written permission from the website creator. Please use the Contact page to obtain relevant permission.





